IP filter in Windows Logon
For terminal server logon(RDP), most people only want to add two factor authentication for external access, they think internal access is safe, so they want to bypass the 2FA for the internal RDP, which we think is quite reasonable.
Our Windows logon solution can obtain the external IP address of the RDP session if the access is from external, even if the RDP client is NATTed in a local network.
In Windows Logon manager, add the internal IP range in IP filter, then the internal access will bypass 2FA, actually you will see the original windows GINA(or credential provider) instead of DualShield GINA(or credential provider).
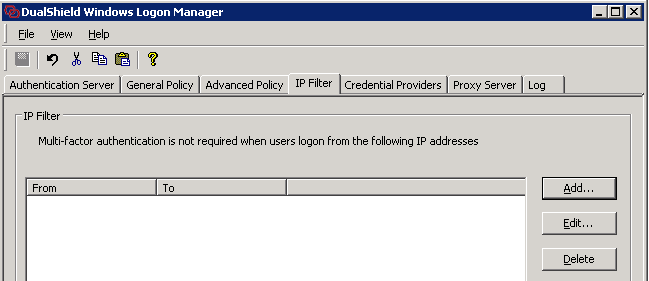
If you have to VPN your internal network first for access the terminal server, we suggest you impose the 2FA on the VPN access. Alternatively, use Windows Logon Solution, but make sure the vpn IP pool is excluded in the IP filter, as the RDP client IP returned by our Windows Logon Solution is within the VPN pool.
What if you connect the terminal server by Remote Desktop Gateway(RDG), well, just exclude the gateway IP in the IP filter. In this situation, the RDP client IP returned by our Windows Logon Solution is IP of the RDG gateway server.
You may notice that Logon Policy also has IP filter settings:
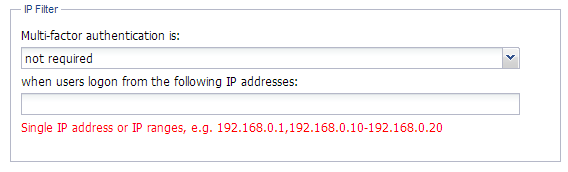
This is different, you will still see our customized Logon Credential Provider (interface).


