NPS as RADIUS Proxy
Network Policy Server (NPS) allows you to create and enforce organization-wide network access policies for client health, connection request authentication, and connection request authorization. When you use NPS as a Remote Authentication Dial-In User Service (RADIUS) proxy to forward connection requests to DualShield RADIUS server, the authentication will be more secure with Deepnet two factor solutions.
Configuration
With the following diagram,
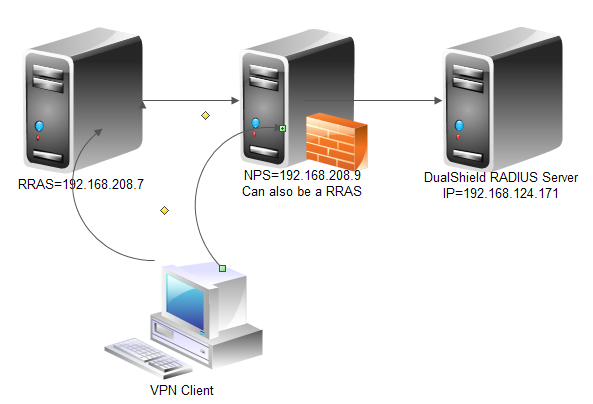
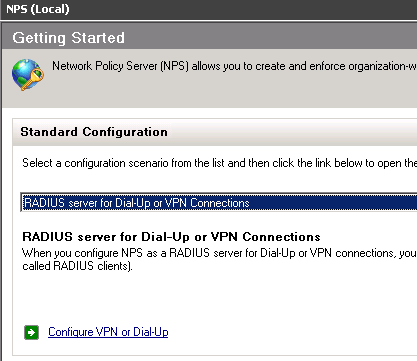
Let us configure NPS as RADIUS proxy to DualShield RADIUS server, you can use NPS wizard for simplicity.
Afterwards, you should review the configuration generated by the wizard.
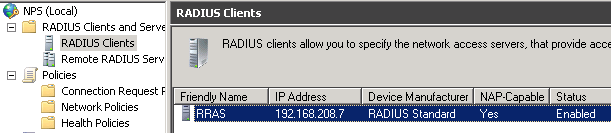
First of all, make sure NPS has a RADIUS client which is the RRAS server.
Next, you should have DualShield Radius server (192.168.124.171) in Remote RADIUS Server Groups, you can create a dedicated group, or just put the server in the built-in Microsoft Routing and Remote Access Service Authentication Servers.
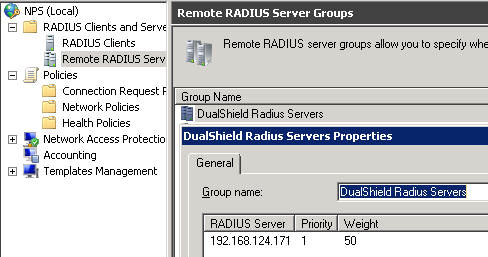
In order to forward the RADIUS request, you need a CRP (Connection Request Policy), make sure the condition(s) will be met. In this example, we simply set the day and time restrictions to ALL DAYS. Only the conditions are met, then settings will be applied. As you can see, in this example, Authentication Provider = Forwarding Request.
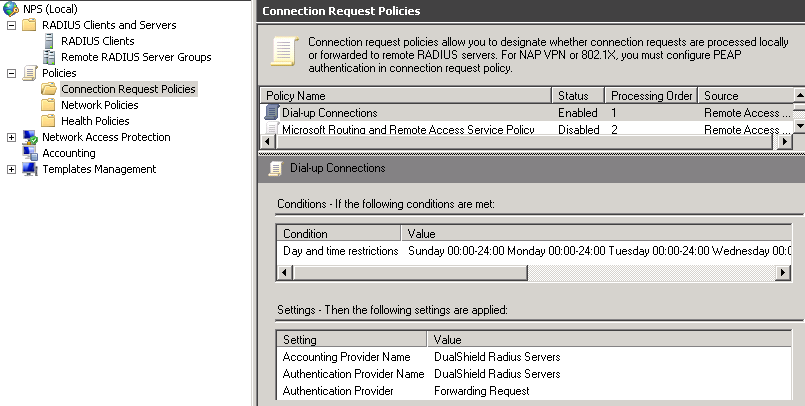
You also need a Network Policy, in which you can setup Session timeout and/or Idle timeout apart from granting the access.
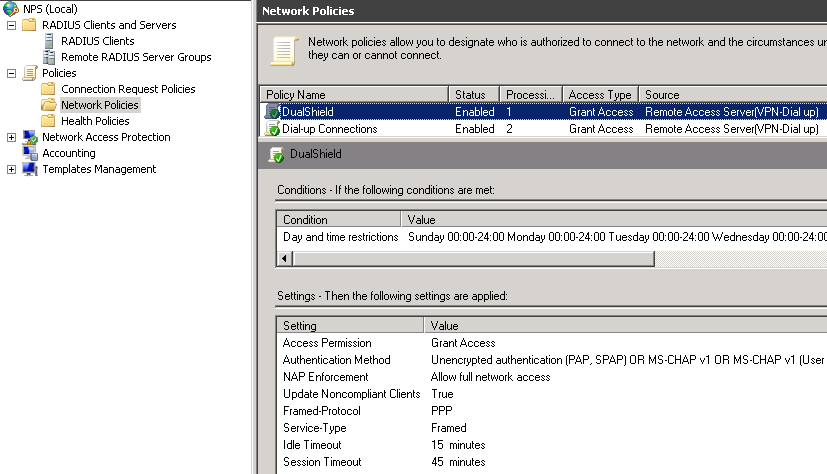
Now you can do the test (VPN connection), assume you have configured all necessary parts at DualShield side (see the details in VPN & RADIUS - Implementation Guide.pdf). In DualShield Audit, you should expect to see some records.
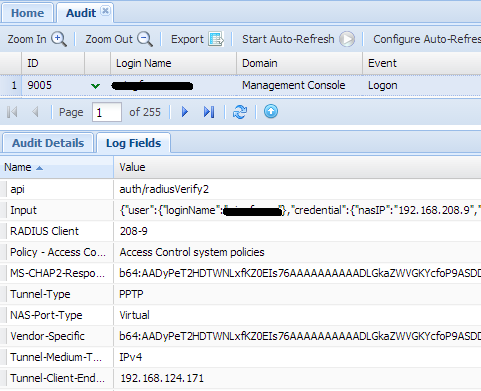
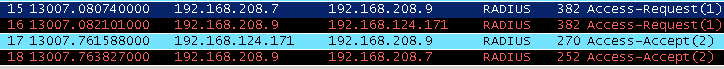
You can double confirm it by sniffering the traffic with WireShark.
In Wireshark, you can see, NAS (192.168.208.7) sent a RADIUS access request to NPS (192.168.208.9), then NPS forwarded the request to DualShield RADIUS server(192.168.124.171).
Once the authentication is done, DualShield RADIUS server sent Access Accept back to NPS, NPS forwarded it to the originator NAS (192.168.208.7)
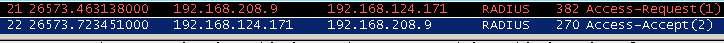
Note: Id you use the RRAS installed on same machine where NPS is installed, then you will see,
Troubleshooting
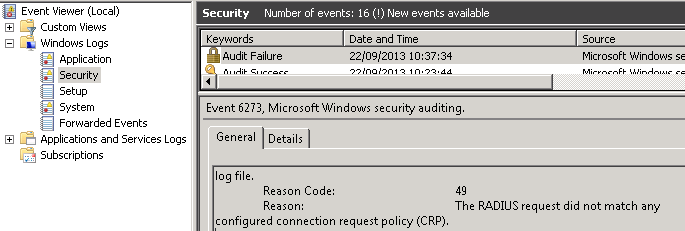
In order to use NPS, your NAS (e.g. RRAS) must be NAP-capable. If you has RRAS on Windows 2003, then you are likely to get error "The RADIUS request did not match any configured connection request policy (CRP)." shown in Event Viewer on NPS server.
If you are unlucky, for instance, there is not radius traffic forwarding to DualShield radius server, then please check Event Viewer. Generally you can see the failure and its reason in Security (under Windows Logs) on NPS server.