Certificate Authentication
Once the authenticator "Certificate" is added into logon step, DualShield supports certificate authentication.
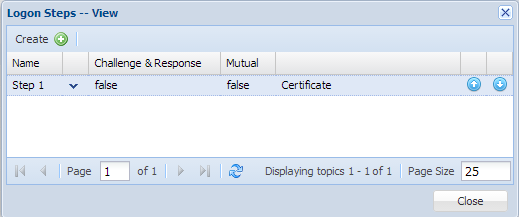
Figure 1
As you can imagine, you have to present a certificate during the authentication
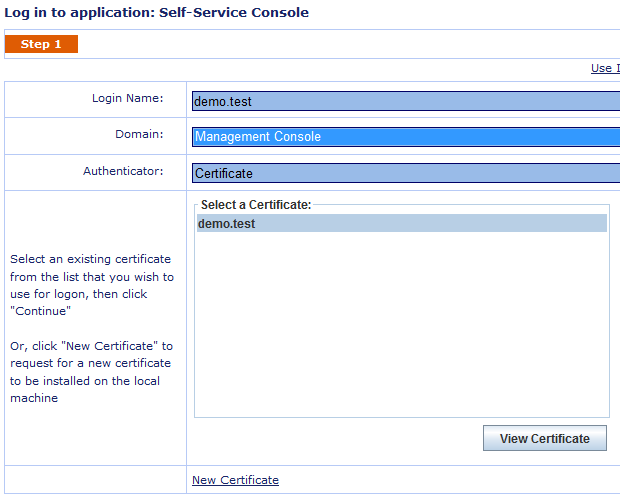
Figure 2
Generally, the certificate is stored in your Windows certificate store which you can view with MMC (Microsoft Management Console)
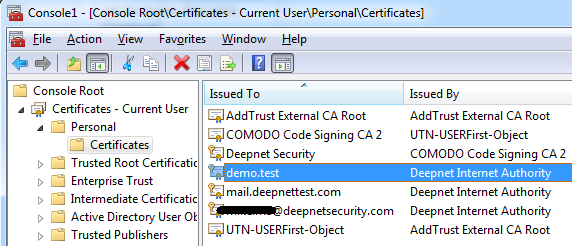
Figure 3
It can also be stored in your smart card, e.g. Aladdin eToken.
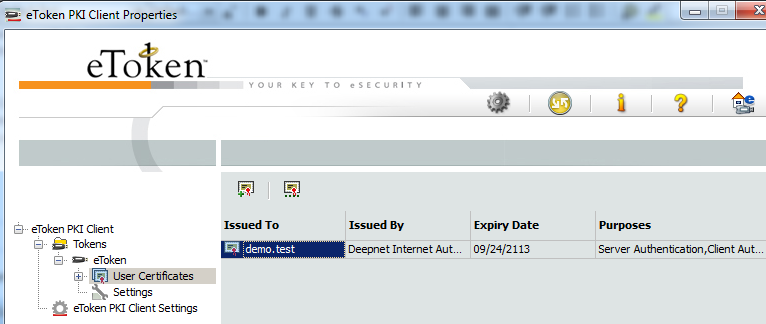
Figure 4
Note: Conventionally each smart card vendor implements soft link in its middle-ware so that the certificates are shown in windows store once the smart card is inserted into the smart card reader. That is why you see "demo.test" in both places(Figure 3 & Figure 4).
If you are a very careful reader, you may ask, why it only lists one certificate in Figure 2 while there are many certificates in Figure 3? Well, DualShield only focuses on the registered ones, which means you have to register a certificate onto a user in DualShield. You can see we only have a registered certificate under the specified user "demo.test".
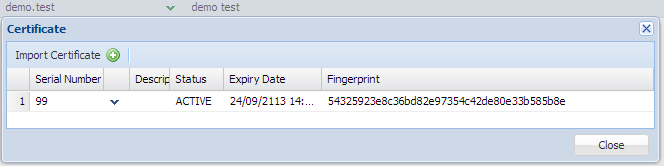
Figure 5
Note: the fingerprint is identical to the one shown in MMC.
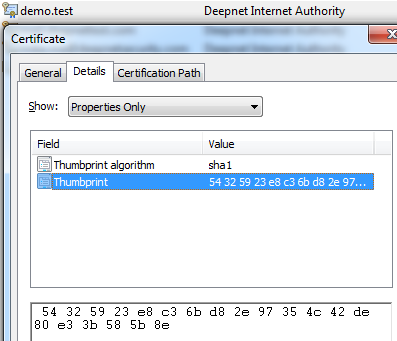
Figure 6
Assume you have a set of certificates in Windows certificate store, let us call it as A, and you have a set of certificates registered on a user in DualShield, let us call it as B. Mathematically, we only list the intersection of A and B
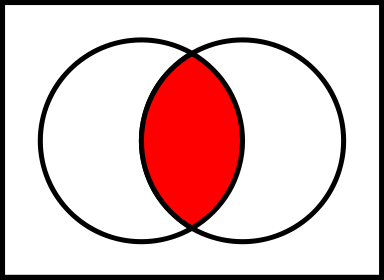
Figure 7
In DualShield, you register a certificate by "Import Certificate",
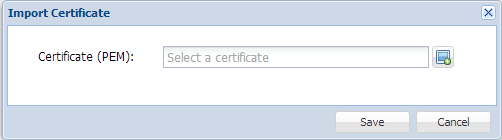
Figure 8
I guess you are going to ask, what is PEM certificate? where can I get it from? Well, certificate is a very techy terminology, you can find a lot of information on Internet. Here let us just put it in simple form. A full certificate contains two parts, private key, and public key (it is also called certificate once it is signed by CA, confused, isn't it?).
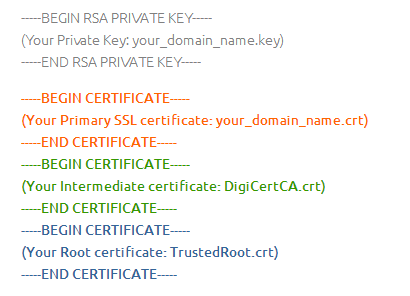
Figure 9
Look at this particular certificate in MMC, it does have a private key.
Without a private key, the certificate is not qualified to do certificate authentication with DualShield.
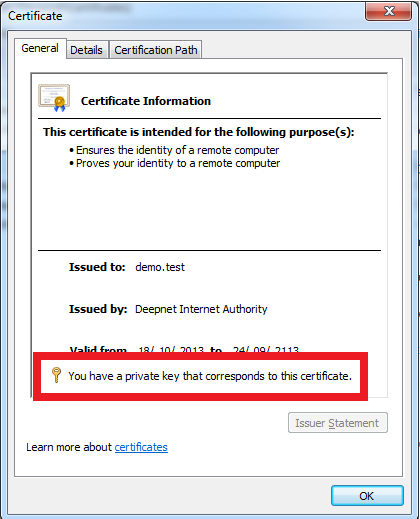
Figure 10
As the name (private key) suggests, it should be owned by yourself. You only give out its counter part, the public key. We call it PEM - (Privacy-enhanced Electronic Mail) Base64 encoded DER certificate, enclosed between "-----BEGIN CERTIFICATE-----" and "-----END CERTIFICATE-----".
You can get it from MMC with "Export..."
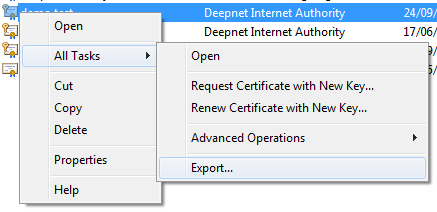
Figure 11
What if I haven't got any certificate on my machine? you may ask. Well, don't worry, you can click "New Certificate" (Figure 2) to create one (generate the private key on your machine, forward the public key to be signed by DualShield CA).
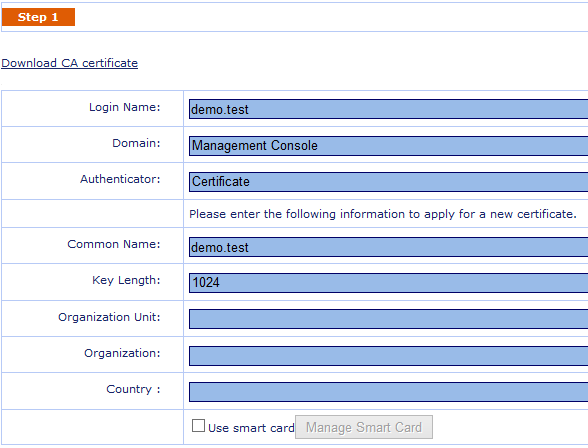
Figure 12
The certificate created with this method is NOT stored in Windows store, instead it is stored as a file in the folder %USERPROFILE%.Deepnet, called certstore.jks.
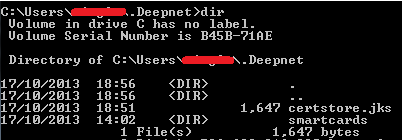
Figure 13
Note: The intersection of sets also applies onto this certificate store.
If you have smart card and want to store the generated certificate onto smart card, then please check the option "Use smart card" (See Figure 12). You need to specify your smart card pkcs11 library. Any decent smart card vendor should provide pkcs11 implementation. Please check with your smart card vendor to get the file name and location. Generally you can tell it by name in the folder c:\windows\system32. For instance,
name = ePass(www.ftsafe.com) |
library = c:\\windows\\system32\\ngp11v211.dll |
name = eToken(www.safenet-inc.com) |
library = c:\\windows\\system32\\eTPKCS11.dll |
name = c3po(www.c3po.es) |
library = c:\\windows\\system32\\FNMT_P11.dll |
The field Slot is quite confusing, so we provide a list function to list on which slot your smart card is.
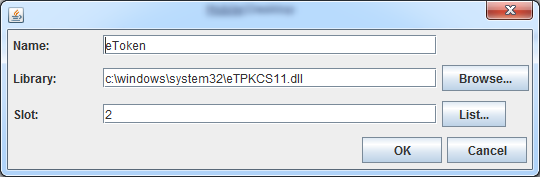
Figure 14
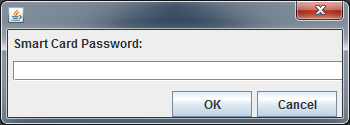
During using smart card, it will prompt a dialog to ask you to type Smart Card Password which has another name PIN.
Under the hood
During the certificate authentication, the server first presents a challenge code to the user. when the user selects a certificate and continue, the client (we use java applet) uses its corresponding private key to do PKI encryption. the submitted content is the encrypted challenge code (not selected certificate). Once the server obtains the content, it uses the certificate (the public key) to do decrytion.


